Multi-factor authentication for synthetics
Exoprise CloudReady synthetic sensors support multi-factor authentication (MFA) testing. This lets you use accounts that require MFA when it's a tenant-wide setting and test the reliability of MFA infrastructure.
MFA background and outages
MFA helps secure logins by requiring an additional authentication factor (source of verifiable secrets). The original factor is something you know (the password). The additional factor is something you have (a dedicated key fob or, more typically, a cell phone running an authenticator app or receiving SMS). For its security benefits, it's not uncommon for MFA to be required tenant-wide. For more information about how MFA works, refer to this Microsoft article.
MFA can also be a point of failure. MFA has been known to cause frustration and even outages when it comes to Azure AD, Entra ID, and Microsoft 365 Services. On September 28, 2021, Microsoft suffered a global outage that prevented customers from logging into their Microsoft 365 accounts. According to the Microsoft Tech support team, the investigation pointed out the root cause of an issue with MFA. Read more about it in this Exoprise article.
Since there have been numerous Microsoft 365 outages related to MFA, it's worth monitoring MFA and being informed of MFA-related login problems.
Exoprise implementation overview
Exoprise supports testing MFA through Time-based One-Time Password (TOTP). TOTP is implemented by authenticator apps like Microsoft Authenticator or Google Authenticator. This is how TOTP MFA works:
-
The server generates a TOTP secret key and shows it to the user as a QR code and a character string.
-
The user imports the TOTP_KEY into an authenticator app.
-
The authenticator uses the TOTP_KEY and the current time to generate a unique and ever changing one-time pass code (TOTP_CODE).
-
The TOTP_CODE is supplied to and verified by the server during login.
-
Because the server and the authenticator both have the TOTP_KEY, they will generate the same TOTP_CODE at a given time, which confirms the user's ownership of the device with the TOTP_KEY.
In order for Exoprise sensors to perform a TOTP-based login, they have to function like authenticator apps, that is, have access to the TOTP_KEY to be able to generate TOTP_CODEs. The TOTP_KEY is supplied to the sensor during configuration and, like passwords, is securely stored with public-private key encryption. For information about the Exoprise Public Key Infrastructure (PKI), refer to Public Key Infrastructure.
At sensor runtime, the TOTP_KEY is utilized to generate the TOTP_CODE and submit it to the login MFA form. The sensor will try to detect and report any MFA-related errors if TOTP_CODE submission fails.
Setting up MFA for synthetic sensors
Obtaining the TOTP_KEY
If the account you are using is not yet registered for MFA, or it is, but you want/need to generate a separate TOTP_KEY for the Exoprise sensors, follow the steps below.
-
If MFA is required but not yet set up, you will be redirected to https://account.activedirectory.windowsazure.com/proofup.aspx during login.
If MFA is already set up, but you need/want to generate a new TOTP_KEY, you can open that page directly.
-
Click Add sign-in method.
-
From the drop-down list, select Authenticator app and click Add.
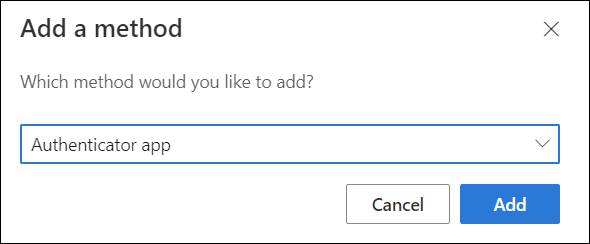
-
You'll be presented with a QR Code and a Can't scan image? option. Click Can't scan image? to generate the secret key.
-
Save the secret key as you will need to supply it in the sensor setup wizard.
If you intend to set up other MFA-based synthetic testing sensors, you should save the secret key; otherwise, you will need to re-register MFA later.
-
To complete the registration, scan the QR code with an existing authenticator app or enter the secret key manually (for example, Microsoft Authenticator, Google Authenticator, or Authy). The authenticator app will then start generating TOTP_CODEs.
-
Click Next to close the pop-up window, and Next again in the main window.
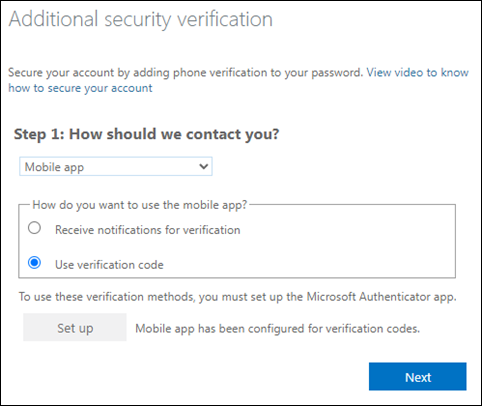
-
To commit the MFA registration, enter the TOTP_CODE from the authenticator app and click Verify.
-
Microsoft may ask for a phone number in case you lose the authenticator.
Supplying the TOTP_KEY to the sensor
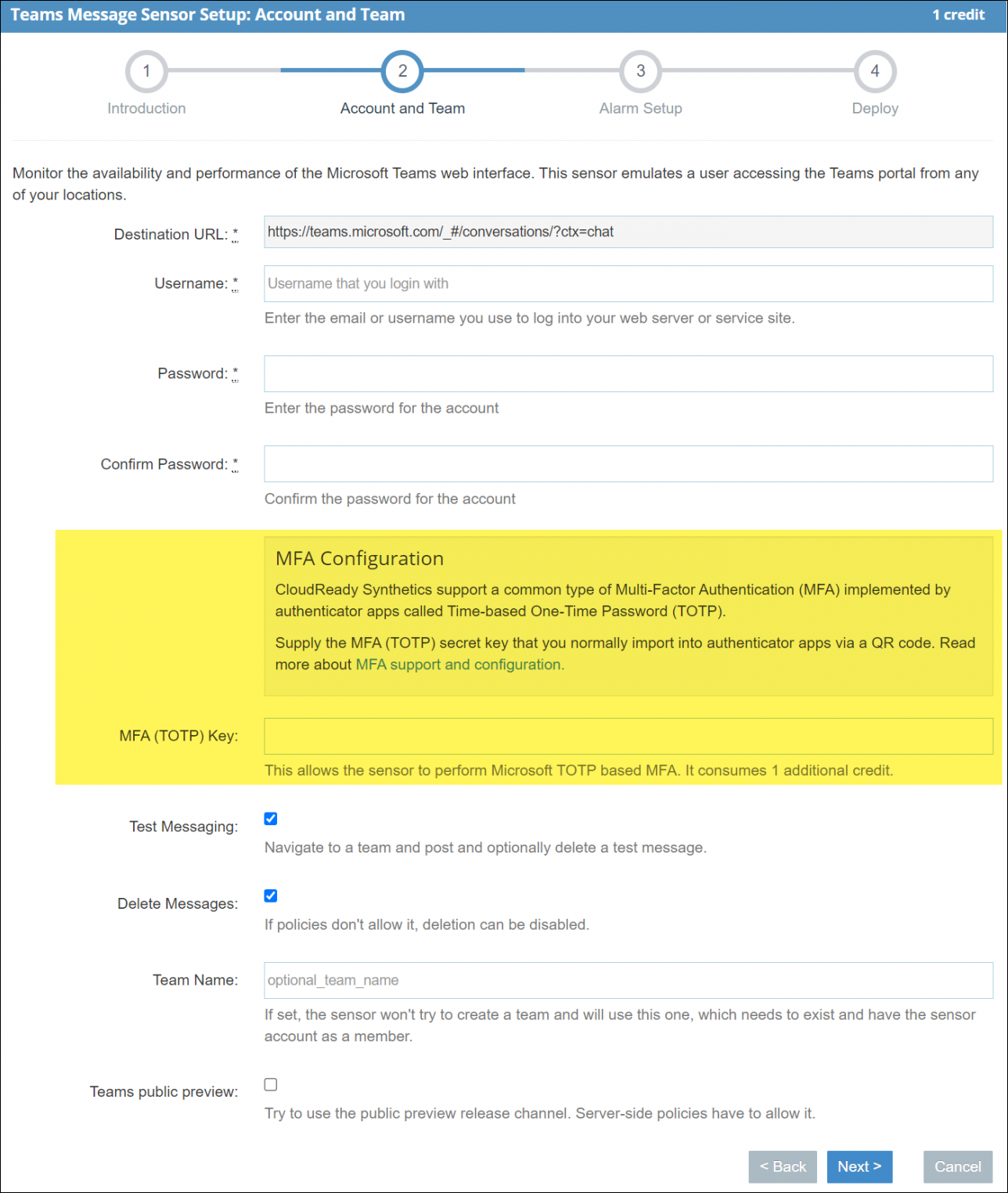
For sensors that support Microsoft TOTP MFA, the sensor config wizard step where you enter credentials will have an optional MFA (TOTP) Key field in addition to the password field. See the following screenshot for an example of testing MFA with Microsoft Teams:
-
Enter the MFA TOTP key.
A synthetic sensor that tests MFA will cost an additional Exoprise credit once deployed.
-
When re-configuring the sensor, the TOTP key won't need to be re-entered unless you want to modify it, in which case you should clear the keep existing option.
Sensor-specific considerations for MFA testing
Outlook Web Access (OWA)
The OWA sensor has two aspects: mailbox access via the EWS API and browser-based mailbox testing via the Outlook Web Access interface for sending test messages. The EWS API requests can be secured by basic authentication (username/password) or OAuth.
Microsoft 365 has two levels of MFA enforcement: enabled and enforced. When enabled, non-web-interactive (EWS API) authentication with the main account credentials continues to work, but when enforced, such authentication is blocked. Therefore, enforced MFA may result in OWA sensor errors like the following:
Autodiscover of the Exchange Web Service URL failed: This account is locked.
Since basic authentication is deprecated, we recommend switching to OAuth as a workaround.