Microsoft Intune integration
Learn how to integrate Microsoft Intune with 1E Shopping for seamless application deployment and management. This guide covers setup requirements, AAD authentication, co-management with Configuration Manager, and admin configurations to streamline software delivery for Windows clients
Using the Microsoft Intune integration is very similar to using Configuration Manager with Shopping for both administrators and end users. The Shopping Microsoft Intune integration supports the Microsoft Intune application types that are most useful for Windows clients. Additional application types might be supported in future versions. Refer to Microsoft Intune applications.
Microsoft update their Azure configuration website frequently, so some screenshots and instructions on this page may not exactly match the latest version. Contact Microsoft or 1E Support if you have difficulties with any of the instructions given below.
It is assumed that you have a working Microsoft Intune and Microsoft Entra ID environment.
The devices used with Shopping's Microsoft Intune integration must be hybrid Microsoft Entra ID joined in Entra ID. User accounts (including administrator and service accounts) must be Windows Server AD sourced in AAD and must have a global domain suffix (for example, Contoso.com, and not Contosocom.onmicrosoft.com). If the accounts are for a local domain, a universal principal name (UPN) can be used.
Microsoft Intune requirements
-
A working Microsoft Intune instance
-
The Clients must be Microsoft Intune-enabled for them to receive Microsoft Intune applications
-
The user accounts must have unique email addresses, that is, Shopping end user accounts cannot share email addresses
-
The relevant Shopping requirements must be met. Refer to Supported platforms and requirements
When the above requirements are met, you can do the following:
-
Define the two required Microsoft Entra ID authentication applications
-
Configure administrator and service accounts. The UPN suffix for these two accounts should match in on-premises AD and AAD
-
Make appropriate settings for Microsoft Intune in Shopping
-
Enable the Configuration Manager co-management feature
Microsoft Entra Connect requirements
Microsoft Entra Connect must be in hybrid mode and have either of these two options enabled:
-
Pass-through authentication with seamless single sign-on (SSO)
-
Federation
Both options are illustrated in the screenshots: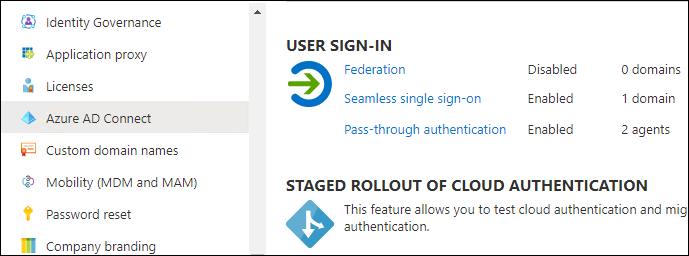
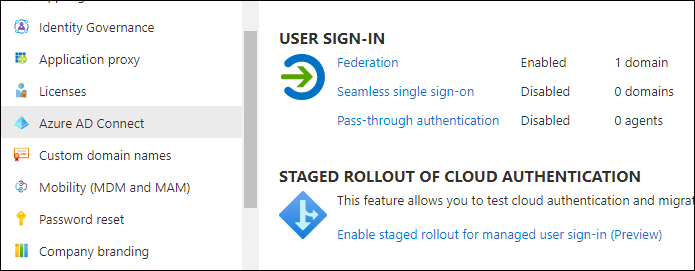
If these options are not available to you, then you must use the Client App Client Secret method of authentication.
The Client Secret method is available only if you install the latest Accumulated Hotfix for Shopping Central.
You will need to configure Microsoft Entra Connect in your on-premises environment. Doing this will add your users from the local domain into your Microsoft Entra ID. Refer to Microsoft Entra Connect and Microsoft Entra Connect Health installation roadmap.
You need the following Microsoft Entra ID accounts:
|
Purpose |
Member of |
Usage and notes |
|---|---|---|
|
Configuration |
Global administrator and Intune administrator AAD roles |
During setup and for troubleshooting. This account performs the steps described in this article. |
|
Service |
Intune administrator AAD role |
Ongoing for the Shopping Central service to access AAD user and device details and app deployment status. This is the AAD hybrid account that corresponds to the service account used to run the Shopping Central service. |
|
Intune administrators |
Intune administrator AAD role |
Ongoing for Microsoft Intune app management. You might prefer to apply the Microsoft Intune administrator role to a group and add relevant administrator accounts to the group. |
|
Shopping administrators |
User and groups setting for the Shopping Console Authentication Client App, refer to Microsoft Intune integration |
To access Microsoft Intune apps from the Shopping console and to trigger on-demand AAD device and user synchronizations. You might prefer to add a group to the User and groups list and add relevant Shopping administrator accounts to the group. The Microsoft Intune administrators and Shopping administrators might all be the same accounts but they do not have to be. Microsoft Intune administrators could manage the Microsoft Intune apps but not have Shopping privileges. Shopping administrators could use the Microsoft Intune apps but not be able to manage them. |
In Microsoft Intune, you'll need to set up two authentication applications for Shopping. These are also known as Authentication Client Apps.
-
Console authentication application: In this example named ShoppingConsoleAuthenticationClientApp
-
Central Service authentication application: In this example named ShoppingServiceAuthenticationClientApp
Use the following steps to create and configure each App. It is vital to get the right configuration in order for Shopping to work with Microsoft Intune. In most cases the configuration steps are the same for each App, and will tell you where they are different, be careful as it is easy to get confused between each App.
We recommended you configure one App at a time, going through the whole sequence of steps. If you want to configure both Apps at the same time, then do so using separate browser windows.
Depending on the version of Microsoft Entra ID you use, although you may see some differences in the UI, the steps required to set up the authentication applications will be the same. Refer to Microsoft Graph permissions reference.
Most of the steps in the sequence are required for both Console and Central Service authentication applications. Where there are exceptions and the instructions apply to one or the other, they will be explicitly called out.
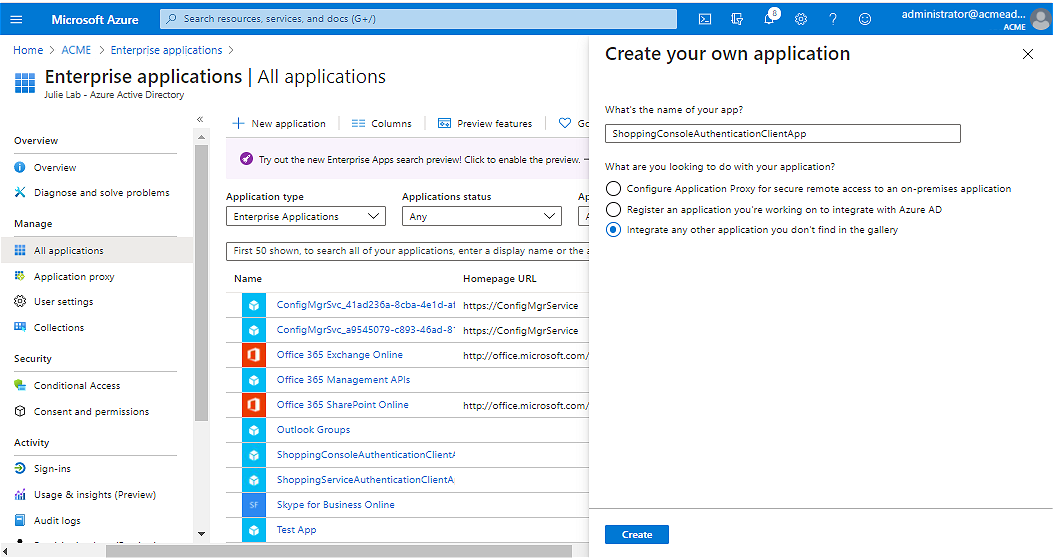
Create your own application
In your AAD console, go to the Enterprise applications node and click New application.
In the Create your own application blade:
-
Provide a name for the application.
-
Console authentication application, in this example named ShoppingConsoleAuthenticationClientApp
-
Central Service authentication application, in this example named ShoppingServiceAuthenticationClientApp
-
-
Select Integrate any other application you don't find in the gallery
-
The application names are not important except for ease of identification. The essential distinction is that one relates to the Shopping console (as used by administrators) and the other relates to the Shopping Central service (as used by Shopping itself).
At this point and similar points where objects are created or adjusted, you should see a success message in the upper right corner of the AAD console.
Note the Application (client) ID
You will then see an Overview tab.
You will need the Application (client) ID when you configure Shopping (as detailed in During installation or upgrade below), so copy it to a text or document file you can reference later. While you can retrieve the Application (client) ID at any time, this is a convenient opportunity to do so.
Ensure you note which application the ID corresponds to:
-
Console authentication application: In this example named ShoppingConsoleAuthenticationClientApp
-
Central Service authentication application: In this example named ShoppingServiceAuthenticationClientApp
Add users and groups to the application
-
On the Overview page, click on the 1. Assign users and groups tile.
-
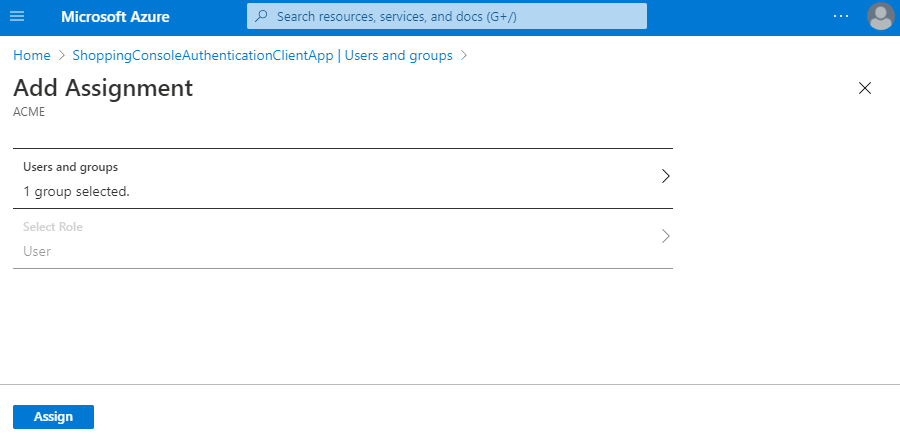
On the Users and groups page, click on Add user (which can also be used to add groups).
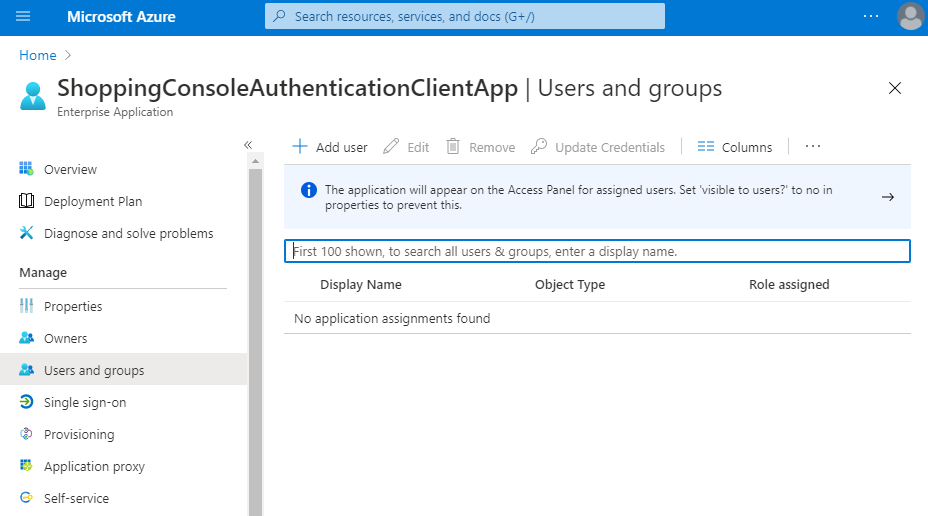
-
Click on the Users and groups None Selected row.
If you are using an evaluation version of AAD, a message will be displayed on this page indicating that groups are not available for assignment. AAD groups are not required for Shopping's Microsoft Intune integration (though it's recommended to use them).
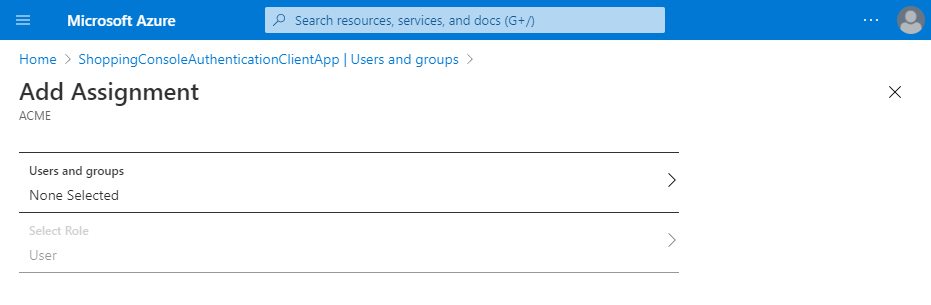
Select from the Users and groups as appropriate.
-
For the Console authentication application, this should be group(s) or users that you expect to use the Shopping console. In our example, for the console app we choose the group ShoppingConsole_Admins used for our Active Directory implementation.
-
For the Central Service authentication application, this should be the Shopping Central service account.
All the accounts or groups have to be from your Active Directory implementation (as opposed to being AAD-only accounts or groups). If you are not sure which are AD users or groups, use another AAD console and review the users and groups under the corresponding nodes. AD users and groups have a source of Windows Server AD.
The users and groups you click on will be listed under Selected Items.
-
-
The number of users and/or groups will be displayed. If this is correct, click Assign.
The users and/or groups will be displayed under the Users and groups node for the application.
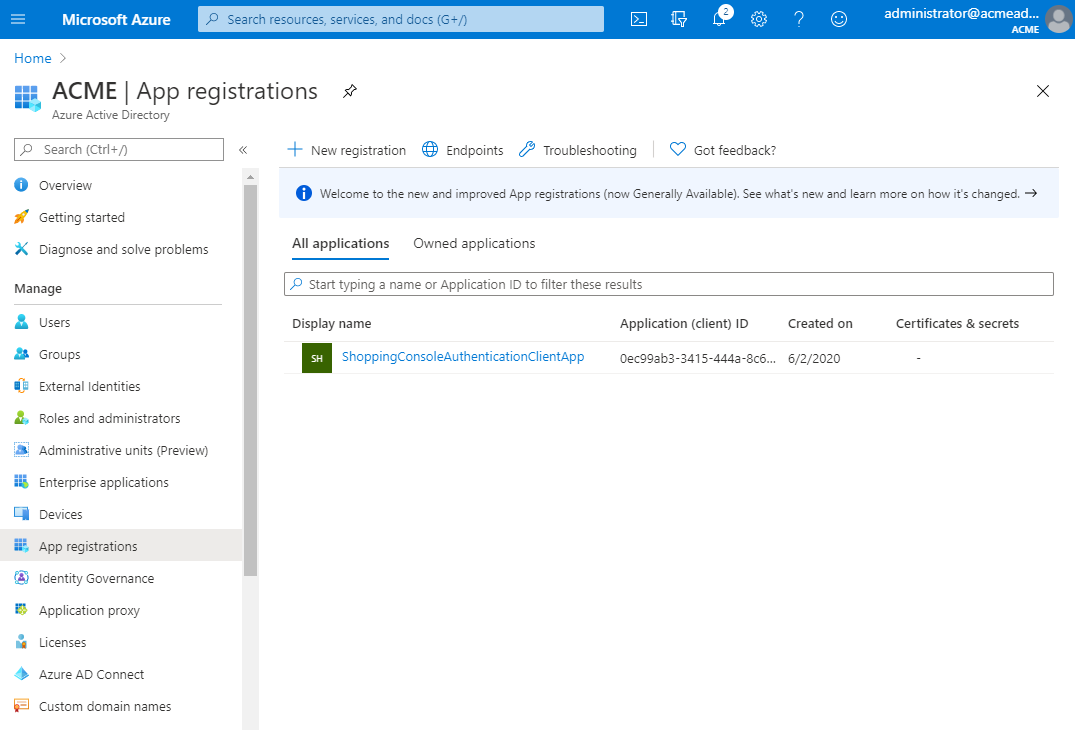
Configure the App registrations
-
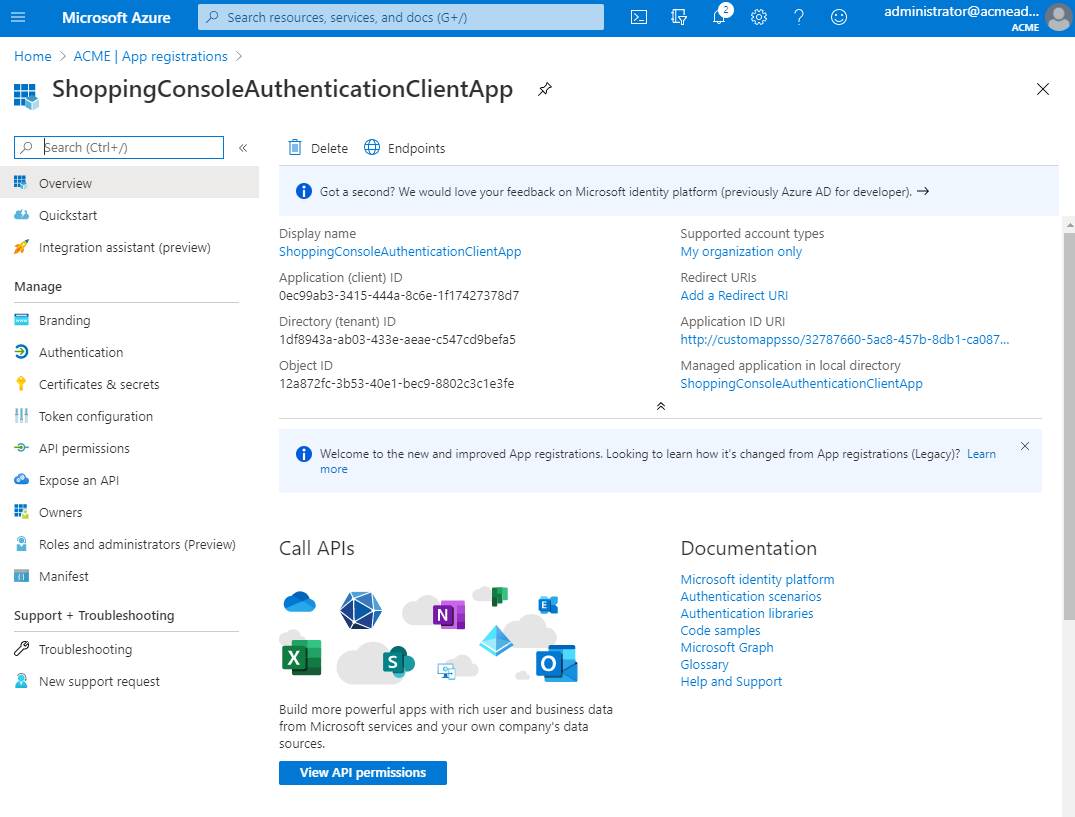
Click the App registrations node of your AAD directory. Click All applications. You will see your application (or applications) listed.
Configure API permissions for the App registration
-
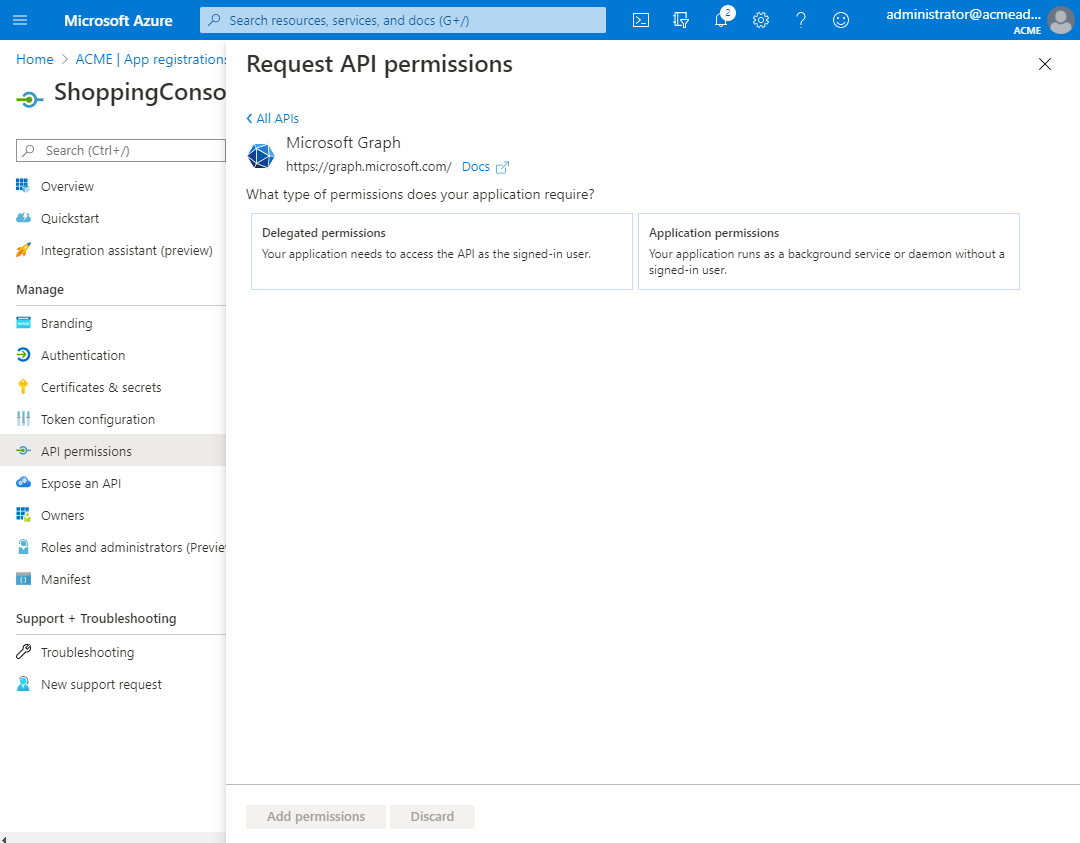
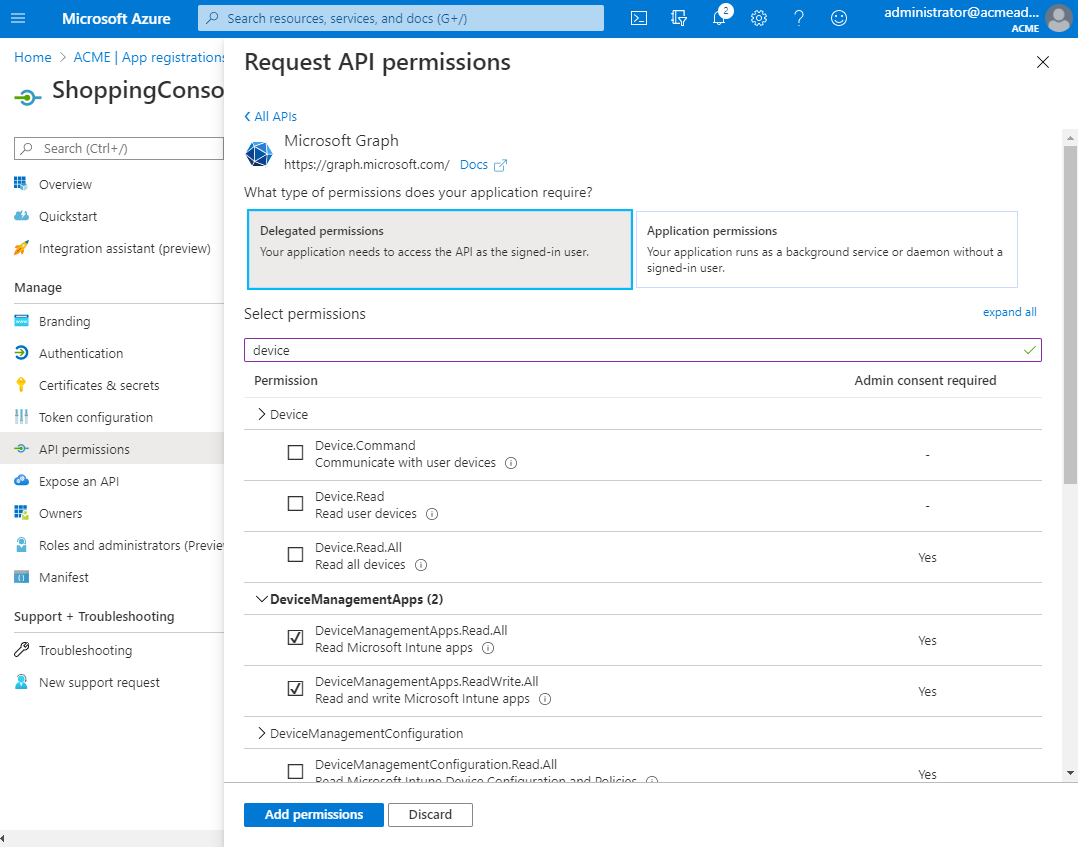
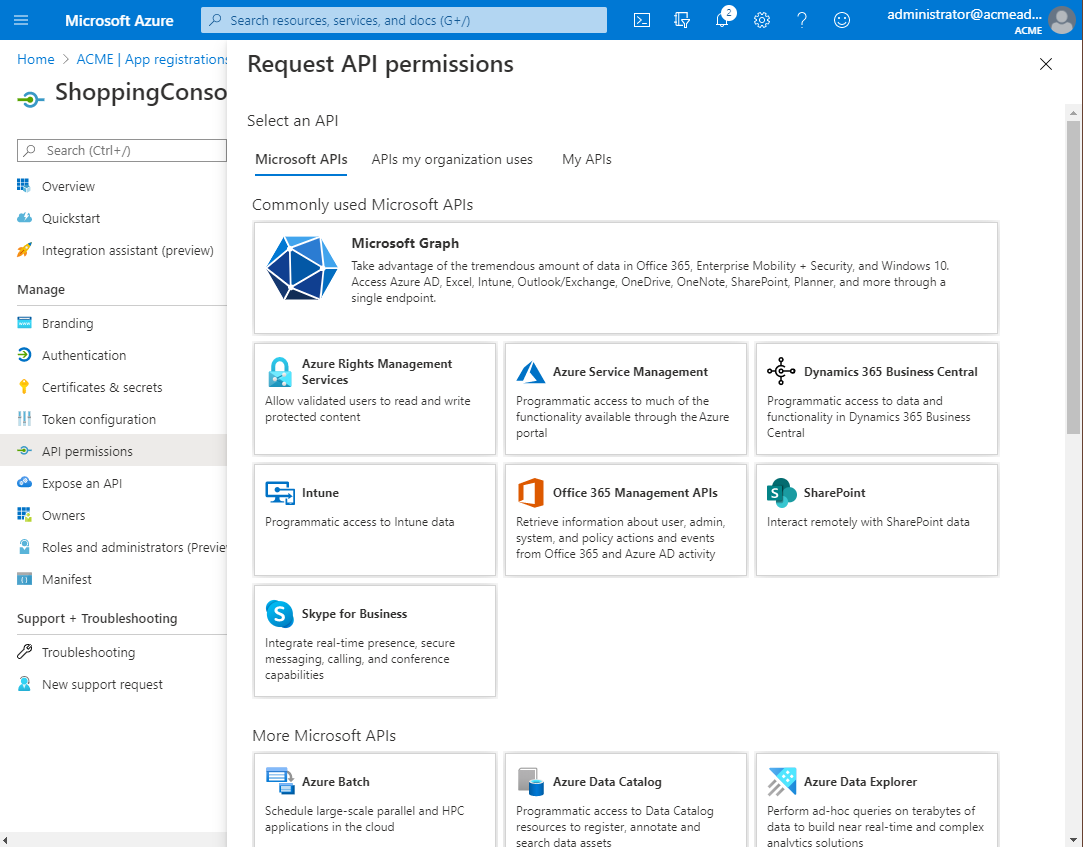
In the Overview node of the selected application, click the API permissions node, then click Add a permission.
-
In the Request API permissions dialog, click the Microsoft Graph tile.
-
Click Delegated permissions/Application permissions based on the authentication.
If you are using Client Secrets and not Seamless SSO, you will need to choose Application permissions. You will also need to create a new client secret.
To add a client secret:
- Click on the Certificates & secrets node and then click on the New client secret button.
- The Add a client secret form will open, add a Description and select an expiry from the Expires radio buttons and then click Add.
- Copy the new client secret value and save it, as you won't be able to retrieve it after you perform another operation or leave this blade.
If you do not copy the Value at this point, when you navigate away from the Certificates & secrets screen, you will be unable to copy it again. This means that you will have to delete the Secret and recreate it.
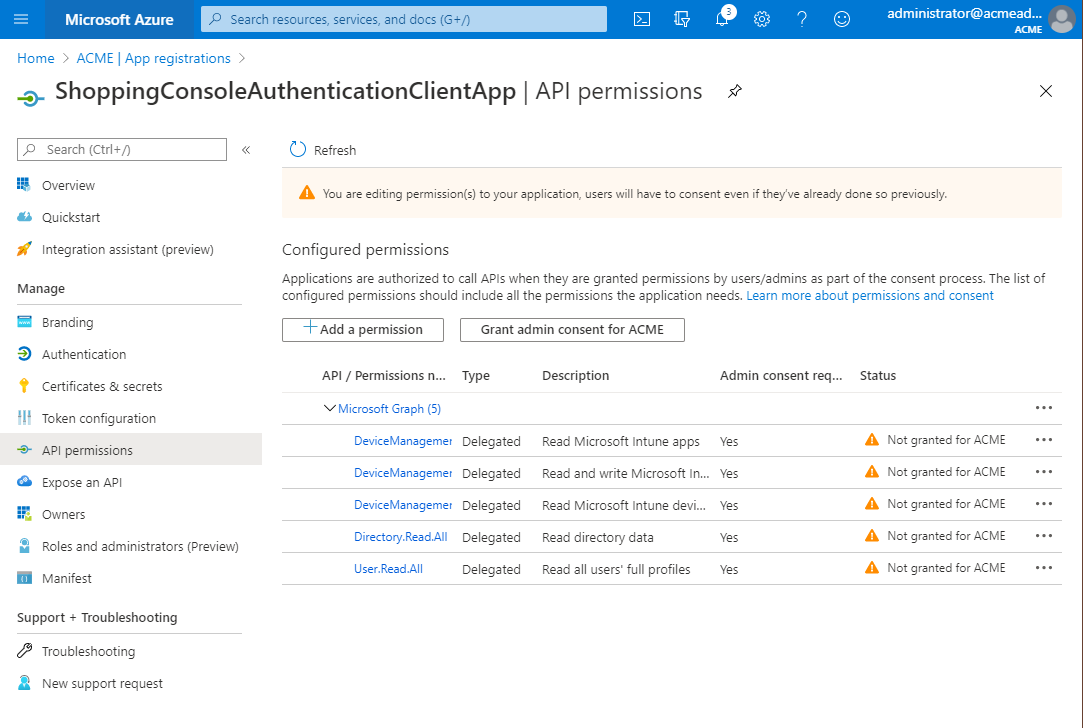
You will see a long list of API permissions, the list will be slightly different depending on whether you are using Application or Delegated permissions. Scroll through them and check them as appropriate, then, click Add permissions.
For the Console authentication application, check the following:
Permission
Purpose
DeviceManagementApps.Read.All
To get application status, application type, and target type.
DeviceManagementManagedDevices.Read.All
To discover devices when the Trigger User and Device Intune Sync button is clicked.
User.Read.All
To get user email address.
Device.Read.All
To get the Microsoft Entra ID of the Intune devices.
For the Central Service authentication application, check the following:
Permission
Purpose
DeviceManagementApps.ReadWrite.All
To get the application status, application type, and target type. Also to create and delete application assignments.
DeviceManagementManagedDevices.PrivilegedOperations.All
To initiate client synchronization (to expedite deployments).
DeviceManagementManagedDevices.Read.All
To discover devices when the Shopping Central service is started and then routinely after that.
Group.ReadWrite.All
To create or remove groups to assign Microsoft Intune applications to that have been added to Shopping.
This is required while creating or removing assignments to a Microsoft Intune application on groups by the Shopping Central Service during the assignment creation process.
GroupMember.ReadWrite.All
To add or remove users or devices from a group, and to verify they've been added or removed as intended.
This is required when adding or removing users or devices to and from a group by the Shopping Central Service during order processing of a Microsoft Intune application.
User.Read.All
To get status when app is user targeted.
Device.Read.All
To get the Microsoft Entra ID of the Intune devices.
-
Click Grant admin consent for <tenant> In our example, the tenant is ACME.
This means that as a tenant administrator for your organization, you're consenting that the users of the application would want to use these permissions. The users in this case would be people that would use the Shopping console and/or set up the Shopping service.
Configure Authentication for the App registration
If you use the client secret method, you do not need to complete the Configure Administrator and Service Accounts steps.
In the AAD console, click Users and select the name of a user that will be a Shopping console user and who might need to manage Microsoft Intune applications or initiate AAD user and device synchronization.
-
Click on the Assigned roles node.
-
Click Add assignments.
-
Check the Directory role called Intune administrator and click Add.
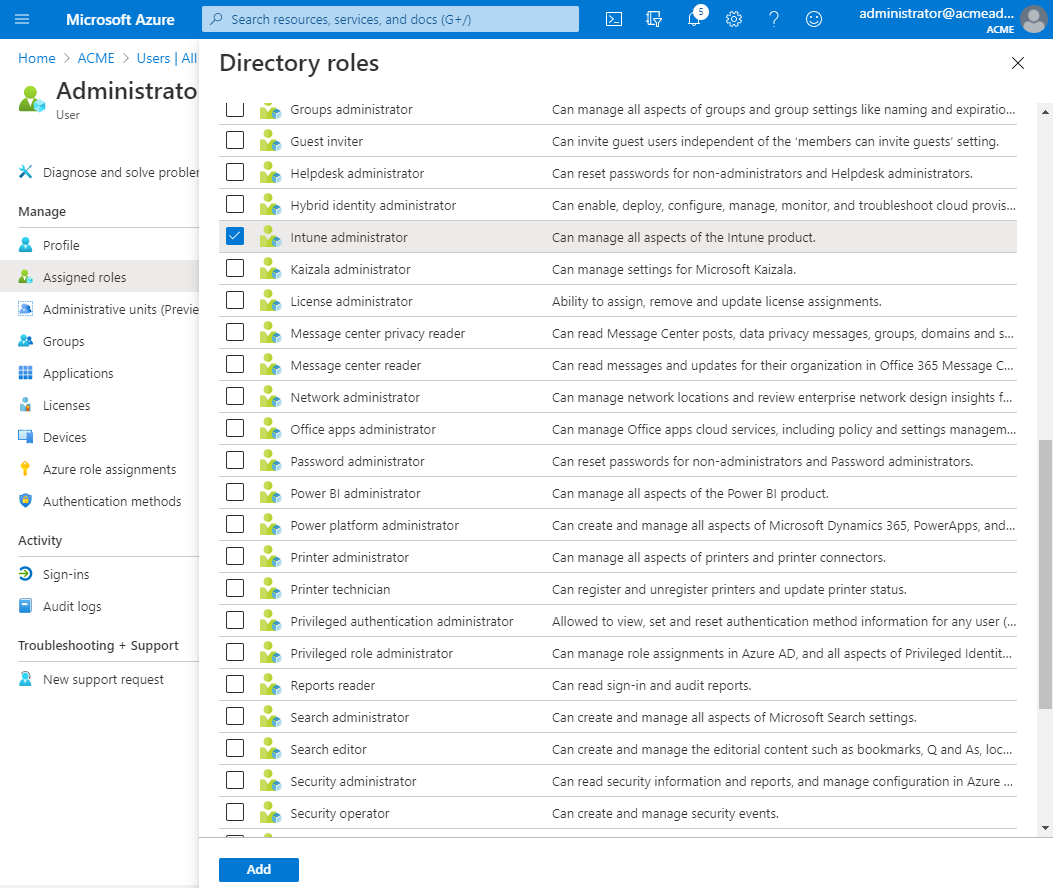
You must repeat this process for the service account used to run the Shopping Central service. Both the Shopping console user and Shopping Central service accounts must be licensed for Microsoft Intune.
The user account must be a hybrid account and so in the list of users the source of the account must be Windows Server AD.
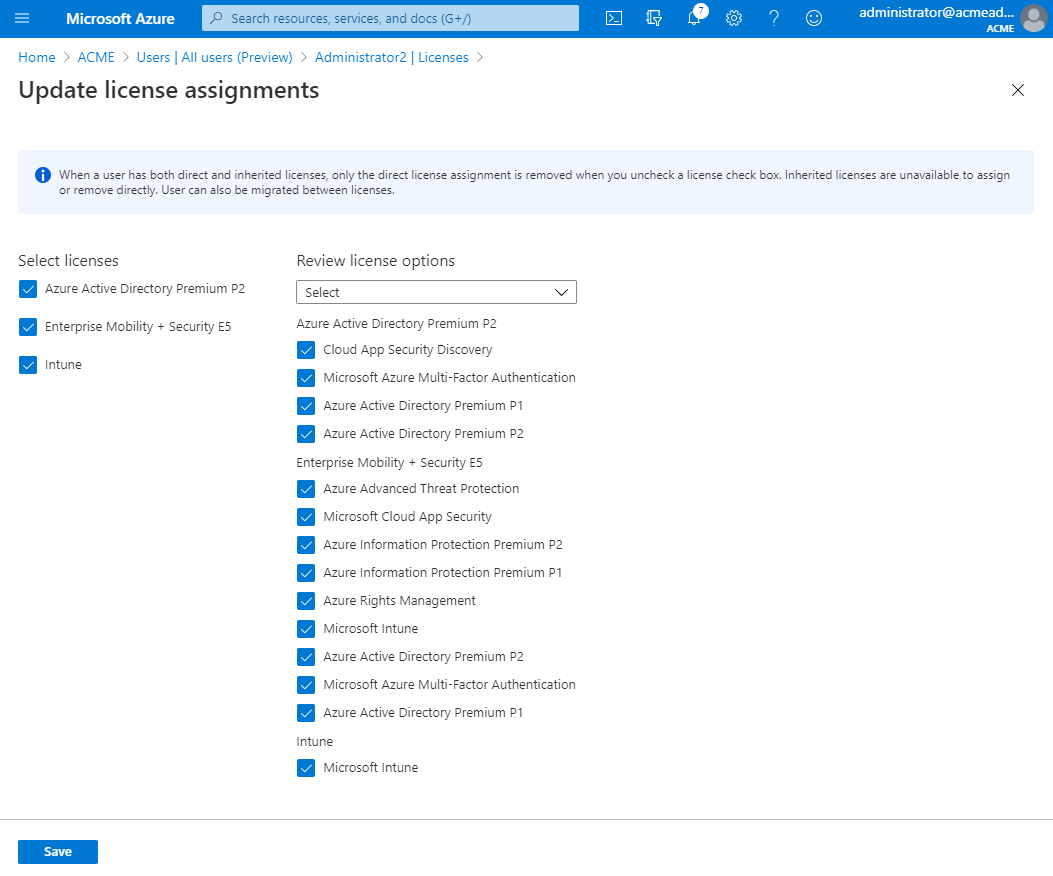
Update license assignments
In the AAD console, go to the list of users and select the name of a user that will be a Shopping console user and who might need to manage Microsoft Intune applications or initiate AAD user and device synchronization. The steps below are also required for the Shopping Central service account to synchronize users and devices from Microsoft Intune.
The usage location for your chosen user and for the Shopping Central Service account must be defined in their User Profile in AAD, otherwise you will get a License cannot be assigned to a user without a usage location specified error.
You can do this either during an installation or upgrade or from the Shopping Admin Console after an installation or upgrade.
During installation or upgrade
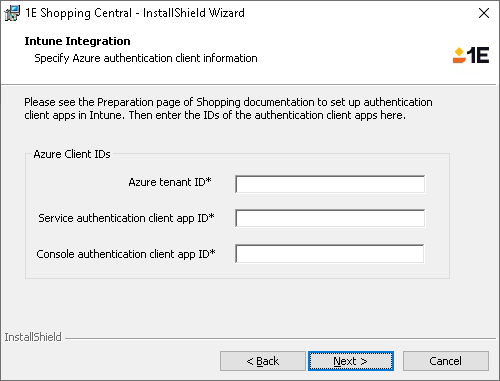
Early in the Shopping Central installation wizard, when you specify the installation type you can indicate whether the Microsoft Intune integration should be enabled by checking Enable integration with Intune.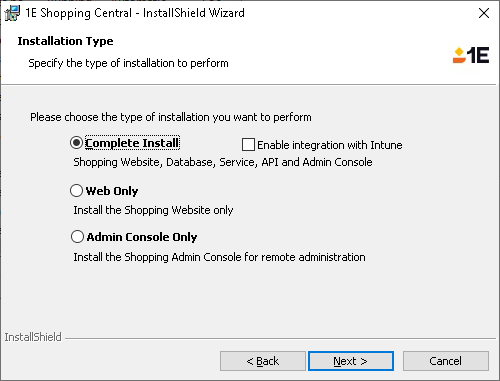
If you enabled the integration with Microsoft Intune, later in the installation wizard you can specify the integration details:
|
ID |
Note |
|---|---|
|
Azure tenant ID |
This is the same as your Azure tenant ID, available in the Overview node of your AAD console. |
|
Service authentication client app ID |
Available in the Overview node for the app in the App Registrations or Enterprise applications nodes of your AAD console. |
|
Console authentication client app ID |
Available in the Overview node for the app in the App Registrations or Enterprise applications nodes of your AAD console. |
After installation or upgrade
You could have enabled Microsoft Intune integration while installing Shopping or upgrading to it. If you did not do so, start the Shopping Admin Console and go to the Intune Integration group of settings in the Settings node.
| Intune Integration |
Note |
|---|---|
| Console Authentication Client App Client Secret |
Client Secret of authentication client app in Azure with limited permissions used by Shopping Admin Console. This setting is available only if you have installed the latest Accumulated Hotfix. |
| Console Authentication Client App ID |
Available in the Overview node for the app in the App Registrations or Enterprise applications nodes of your AAD console. |
| Intune Integration Enabled |
True. |
| Service Authentication Client App Client Secret |
Client Secret of authentication client app in Azure used by Shopping Central Service. This setting is available only if you have installed the latest Accumulated Hotfix. |
| Service Authentication Client App ID |
Available in the Overview node for the app in the App Registrations or Enterprise applications nodes of your AAD console. |
| Tenant Id |
This is the same as your Azure Tenant ID, available in the Overview node of your AAD console. |
| Use Client Secret for authentication with client app instead of seamless SSO |
To use client secrets instead of seamless SSO to acquire authentication token of respective client app to query Intune portal using Graph API calls. This setting is available only if you have installed the latest Accumulated Hotfix. |
Click Save.
Restart the Shopping Central service and then the Shopping Admin Console.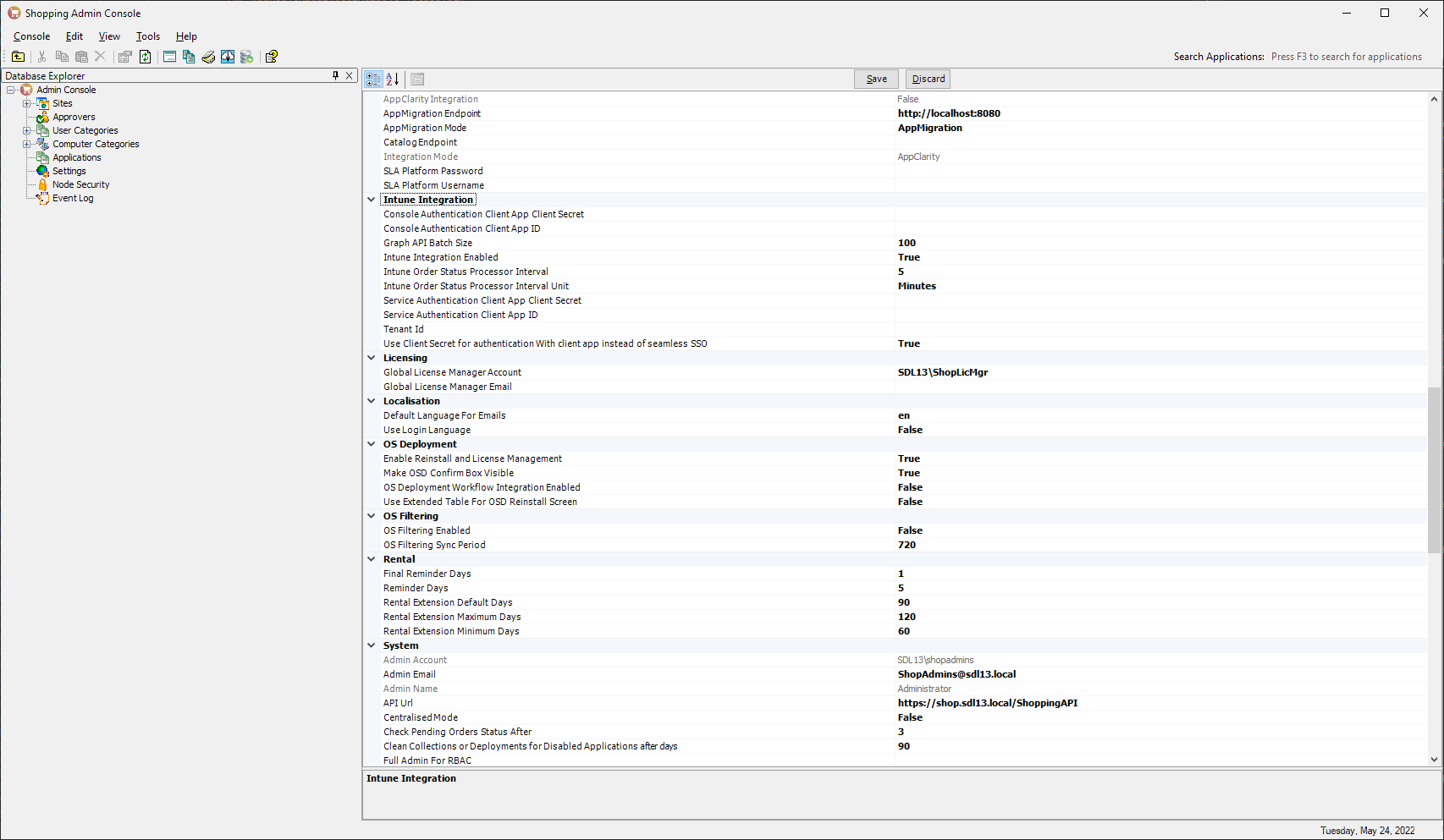
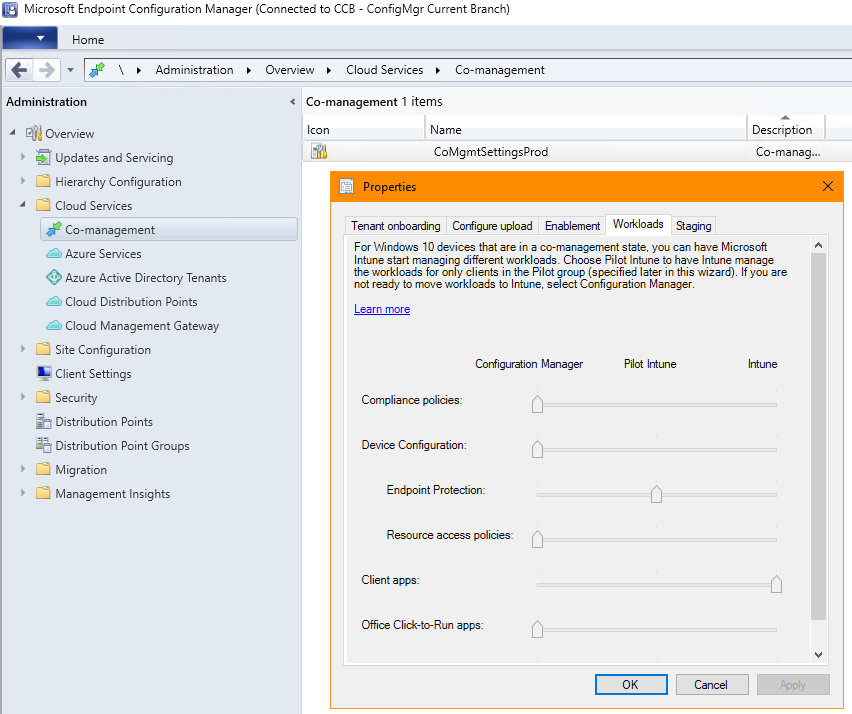
This section describes where the co-management settings would be configured by a Configuration Manager administrator. The Microsoft Intune clients will not try to do software distribution if this feature is not enabled. Refer to your Configuration Manager documentation for full instructions on how to configure co-management. No additional configuration is needed in Shopping to support this feature.
-
Using a ConfigMgr console, in the Administration node, under Cloud Services, Azure Services, in the ribbon click on Configure Azure Services and add Cloud Management.
-
Under Cloud Services, Co-management, configure the co-management.
-
Set Client apps to use Intune.
-
The ConfigMgr clients must be restarted to reflect these changes (as reflected in the client-side CoManagementHandler log).
After a successful installation, the Shopping Central service automatically removes the target device from the associated Microsoft Entra ID group. This behavior is analogous to how devices are removed from SCCM collections following deployment completion.
Log Verification
To verify that the cleanup process has occurred, refer to the Shopping Central logs. The relevant activity is logged by the thread named:
IntuneCleanupAfterOrderCompletionProcessor_<i>Look for a log entry similar to the following:
Successfully triggered sync for device <DeviceName> after removing it from AAD group.This entry confirms that:
-
The device was successfully removed from the Microsoft Entra ID group
-
A synchronization operation was triggered post-removal
You are now ready to use Shopping with Microsoft Intune. If you have appropriate applications set up in Microsoft Intune, you can define the applications in Shopping (refer to Microsoft Intune applications for details) so that they can be made available to users.
Users can then request the applications from the Shopping web interface. The applications will be delivered by Microsoft Intune and their status will be returned to Shopping. The features of Shopping, such as approvals and rentals, can be used with these applications.
Here is a list of frequently asked questions regarding the integration:
Why do I get 0 devices and 0 users discovered when I review the Shopping Central log?
The Microsoft Intune/AAD infrastructure itself might not be properly configured or the Service Account is not properly configured.
Why are no Microsoft Intune applications listed when I'm creating a Microsoft Intune Shopping application?
Ensure that user and device discovery are working correctly to ensure that your basic Microsoft Intune and integration functionality is working. If so, the problem is almost certainly with the account used by the Shopping Console application. Ensure it is configured properly, as per the prerequisites.
Why do I get 0 devices and 0 users discovered when clicking the Trigger User and Device, Intune Sync button?
Most likely because the console-specific Shopping AAD enterprise app is not set up properly.
Why does Shopping say "The Intune application is not available for shopping on machine as it is not a valid Intune machine"?
The most likely cause is that the server-side Shopping/AAD sync has not happened since the Microsoft Intune client was set up. You can initiate that sync at any time from the Shopping console using the Trigger User and Device Intune Sync button.
Another reason for this error is if the client can't be identified by the Shopping agent. This could be true if localhost web queries are blocked.
Why does Shopping not show Microsoft Intune Apps even when the machine is a valid Microsoft Intune machine?
The most likely cause is that the server-side Shopping/AAD sync has not happened since the Microsoft Intune client was set up. You can initiate that sync at any time from the Shopping console using the Trigger User and Device Intune Sync button.
Also if 1EClient is not updated to v5.0 and hotfix Q21071 or later is not applied. Older 1E Client overrides Microsoft Intune information of
machine even if server-side sync has successfully completed.