Endpoint Automation
Endpoint Automation is based on the concept that a device is aware of its own current state more accurately than any centrally held repository. Also, if you can query the device directly then the need to store masses of data becomes unnecessary.
Endpoint Automation Concepts
Concepts used by the Endpoint Automation application, which ensures device compliance with enterprise IT policies. Endpoint Automation allows you to easily check and enforce device state. Device state can represent just about anything you'd like to be set in a certain way for a collection of devices.
Before using Endpoint Automation you need to configure it and upload some policies (with their rules, triggers and preconditions), refer to:
Once you have imported a DEX Pack you can configure and deploy policies to manage various device attributes. For example:
-
Registry keys.
-
Services.
-
Config Manager metrics such as client cache usage.
-
Disk free space.
-
WMI namespaces and classes.
Policies and Rules
Endpoint Automation is enforced by the 1E Client at each device using one or more policies that are deployed to devices according to their management group memberships. A policy consists of one or more rules, which fall into two primary categories:
|
Category |
Explanation |
|---|---|
|
Allow you to verify that a device has a particular state, such as a registry key having a specific value. You can then view summary and detail reports which show devices that are compliant and not compliant with the check rules. |
|
|
Allow you to define a desired state for the device and then enforce that state. For example, you could mandate that a registry key exists and contains a specific value. Again, you can report on the application of these fix rules to devices. |
Management groups use rules to determine device membership, enabling the devices to be administered as a group. For example, you can select devices based on their Active Directory Organizational Unit, or their operating system version, or any other criteria available to the management group rules. refer to Management Groups page for details.
Fragments
Fragments is a collective term for rules, trigger templates, and Preconditions which are written in SCALE.
Triggers
Triggers define the conditions which will cause a rule to be evaluated. Each check rule and fix rule must have a rule trigger defined using a trigger template.
Preconditions
Both check rules and fix rules may have optional preconditions defined. Preconditions allow you to define a conditional test that must be met before the rule is evaluated.
A precondition is not required. If you do not specify a precondition, then the rule is always evaluated when the trigger fires.
Dependencies
Check rules require a:
-
Trigger.
-
Check.
You can also optionally add a precondition.
Fix rules require a:
-
Trigger.
-
Check.
-
Fix.
You can also optionally add a precondition.
Be sure that you understand the key differences between Check Rules and Checks and Fix Rules and Fixes:
-
A Check Rule defines a Check, including a trigger and optional preconditions.
-
A Fix Rule defines a Check and a Fix, including a trigger and optional preconditions. a fix is applied when a check is performed and the check result indicates a compliance failure.
Rule outcomes
A rule always returns two items to the platform subsystem. One is a Pass/Fail value and the second is an arbitrary data item. A rule can also return an error status to the subsystem. This can occur if the rule logic terminates unexpectedly, for example, because a file could not be found etc.
Endpoint Automation history will show the result of rule evaluation. It will clearly indicate whether a check rule returned a success (compliance), failure, or error. It will also show whether a fix rule (if applicable) indicated success, failure, or returned an error.
Four things you should know about rule outcomes:
-
A check or fix rule that fails or results in an error causes a device to remain non-compliant from a Endpoint Automation perspective.
-
History entries are only created in Endpoint Automation when an overall compliance transition occurs, for example from false to true or true to false.
-
If the precondition for a rule returns failure on a device when evaluated, then the Endpoint Automation subsystem indicates 'not applicable' against the device compliance status for the rule.
-
Rules that return 'not applicable' do not affect device compliance status. If all rules for a device returned 'not applicable' the device would still be regarded as compliant.
Endpoint Automation Features
An overview of Endpoint Automation features. The Endpoint Automation application gives you the ability to ensure device compliance with enterprise IT policies.
1E provide Integrated Product Packs contain some ready-made policies. refer to Configuring Endpoint Automation for more details.
Policies and Rules
The Endpoint Automation of a device is enforced by the 1E Client at the device. One or more policies are deployed to devices according to the management groups the devices belong to. Each policy consists of one or more rules that are either check rules or fix rules.
|
Rule |
Explanation |
|---|---|
|
Check |
Allow you to verify that a device has a particular state, such as a registry key having a specific value. You can then view summary and detail reports which show devices that are compliant and not compliant with the check rules. |
|
Fix |
Allow you to define a desired state for the device and then enforce that state. For example, you could mandate that a registry key exists and contains a specific value. Again, you can report on the application of these fix rules to devices. |
For an explanation of management groups, refer to the Management Groups page. Management groups allow devices to be flexibly grouped, based on management group rules. This means you can easily administer devices based on, for instance, their Active Directory Organizational Unit, or their operating system version, or any other criteria supported by the management group rules. Refer to Defining your own policies and 1E DEX Packs reference
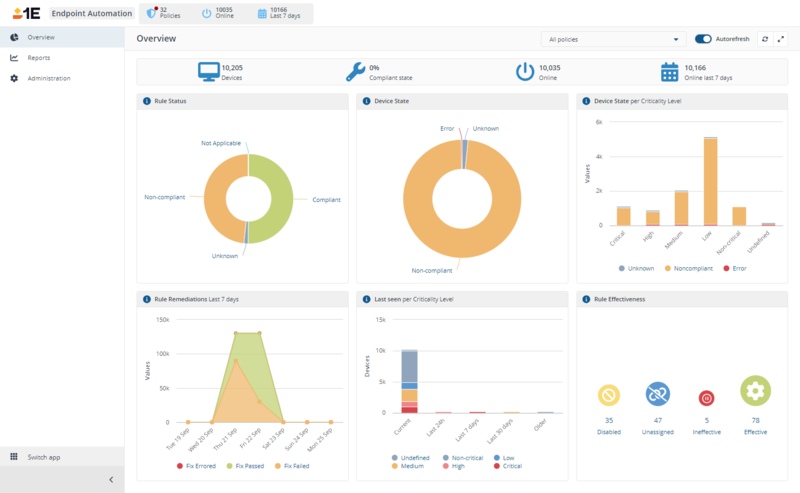
The Endpoint Automation Overview page
The Overview page lets you view the current state of your enterprise in terms of the devices and policies that have been defined and applied. It consists of a number of charts that let you monitor the state in real-time. Refer to Overview and Reports pages
Endpoint Automation Reports
The Endpoint Automation application provides three reports that let you view the details for the currently defined Policies, Rules and Devices. The information in these reports is consolidated into the Endpoint Automation Overview page charts. Refer to Overview and Reports pages
Exploring devices
Endpoint Automation provides a Devices page where you can view the currently connected devices. On this page you can also select one or more of the devices and click Explore that launches the Explorer application. You can then run an instruction using the selected devices as the coverage for the instruction. Refer to Using Endpoint Troubleshooting to investigate devices in Endpoint Automation
Device Criticality
Device criticality is an attribute of a device that defines its importance within an organization. The default definition in the platform has these settings:
-
Undefined (or not set).
-
Non-critical.
-
Low.
-
Medium.
-
High.
-
Critical.
At present, criticality settings do not affect the primary operation of Endpoint Automation. However, it is possible to use the platform to set device criticality and to view it within Endpoint Automation.
The platform also supports the use of the criticality setting when defining coverage for an instruction. For example, you can target an instruction to be sent only to devices whose criticality is not Critical. Refer to Using device criticality